Hello,
I’m looking for either help with understanding the possibilities of the current implementation of custom OIDC or to propose enhancement(s) in that area.
Bit of background.
- We are using Auth0’s multiple connections model in our multi-tenant application. In this model tenants data is stored in different connections - realms.
- Every app in our hosted Squidex is a tenant matched to the tenant from our application.
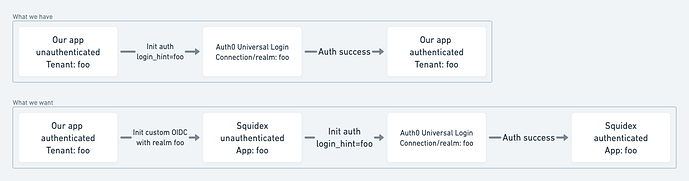
- We would like to configure OIDC in Squidex in such a way that authentication flow can be initiated in our app and via Auth0 land user authenticated in Squidex in the same tenant (app).
- Auth0 Universal Login which we use for auth can be loaded with realm information passed in via
login_hintparam (as described here). This is what we already do in our app and would like to be able to do in Squidex.
Here are my questions.
- Is there an endpoint in Squidex I can send a user from our app to that will trigger custom OIDC auth and ignore all other configured auth methods?
- Is there a way to send realm information from Squidex to configured custom OIDC (as described here)? Can realm value by dynamic?
- Is there a way to redirect user to the resource they were trying to reach after successful auth via custom OIDC? Consider this. From our app a link will take authenticated user to Squidex, say
/app/foo/content/my-schema?pageSize=10. If there’s no auth session in Squidex, I’d like Squidex to just use configured custom OIDC endpoint (ignore all other auth methods I might have configured), extract app name (foo), add it to the OIDC endpoint aslogin_hintparam and send to Auth0. Once Auth0 responds with successful auth, Squidex session is established and my user is taken to/app/foo/content/my-schema?pageSize=10.