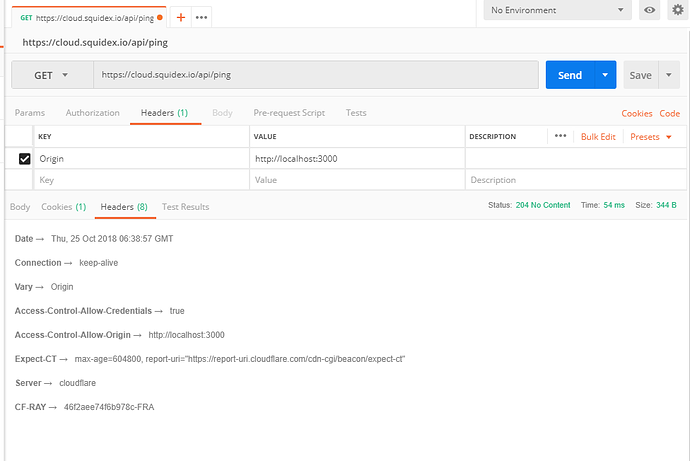
Sure: https://gist.github.com/bschulz87/69b037fcacb1a548ea29d2c78ef689ea
I also included my docker-compose.yml - i use Traefik with forced https.
After trying the /identity.server/connect/token to get a token i get this new errors:
squidex_1 | {
squidex_1 | “logLevel”: “Warning”,
squidex_1 | “message”: “CorsPolicyService did not allow origin: http://localhost:1234”,
squidex_1 | “origin”: “http://localhost:1234”,
squidex_1 | “app”: {
squidex_1 | “name”: “Squidex”,
squidex_1 | “version”: “1.0.0.0”,
squidex_1 | “sessionId”: “37f4288b-a980-4e46-9a2e-aaa8f3e65a4f”
squidex_1 | },
squidex_1 | “web”: {
squidex_1 | “requestId”: “d2092ece-e906-4351-bdcc-28688ba92990”,
squidex_1 | “requestPath”: “/connect/token”,
squidex_1 | “requestMethod”: “POST”
squidex_1 | },
squidex_1 | “timestamp”: “2018-11-18T11:49:18.1472664Z”,
squidex_1 | “category”: “IdentityServer4.Hosting.CorsPolicyProvider”
squidex_1 | }
squidex_1 |
squidex_1 | {
squidex_1 | “logLevel”: “Information”,
squidex_1 | “message”: “Invoking IdentityServer endpoint: IdentityServer4.Endpoints.TokenEndpoint for /connect/token”,
squidex_1 | “endpointType”: “IdentityServer4.Endpoints.TokenEndpoint”,
squidex_1 | “url”: “/connect/token”,
squidex_1 | “app”: {
squidex_1 | “name”: “Squidex”,
squidex_1 | “version”: “1.0.0.0”,
squidex_1 | “sessionId”: “37f4288b-a980-4e46-9a2e-aaa8f3e65a4f”
squidex_1 | },
squidex_1 | “web”: {
squidex_1 | “requestId”: “d2092ece-e906-4351-bdcc-28688ba92990”,
squidex_1 | “requestPath”: “/connect/token”,
squidex_1 | “requestMethod”: “POST”
squidex_1 | },
squidex_1 | “timestamp”: “2018-11-18T11:49:18.1510005Z”,
squidex_1 | “category”: “IdentityServer4.Hosting.IdentityServerMiddleware”
squidex_1 | }
squidex_1 |
squidex_1 | {
squidex_1 | “logLevel”: “Warning”,
squidex_1 | “message”: “Invalid HTTP request for token endpoint”,
squidex_1 | “app”: {
squidex_1 | “name”: “Squidex”,
squidex_1 | “version”: “1.0.0.0”,
squidex_1 | “sessionId”: “37f4288b-a980-4e46-9a2e-aaa8f3e65a4f”
squidex_1 | },
squidex_1 | “web”: {
squidex_1 | “requestId”: “d2092ece-e906-4351-bdcc-28688ba92990”,
squidex_1 | “requestPath”: “/connect/token”,
squidex_1 | “requestMethod”: “POST”
squidex_1 | },
squidex_1 | “timestamp”: “2018-11-18T11:49:18.1511207Z”,
squidex_1 | “category”: “IdentityServer4.Endpoints.TokenEndpoint”
squidex_1 | }
squidex_1 |
squidex_1 | {
squidex_1 | “logLevel”: “Information”,
squidex_1 | “elapsedRequestMs”: 4,
squidex_1 | “app”: {
squidex_1 | “name”: “Squidex”,
squidex_1 | “version”: “1.0.0.0”,
squidex_1 | “sessionId”: “37f4288b-a980-4e46-9a2e-aaa8f3e65a4f”
squidex_1 | },
squidex_1 | “web”: {
squidex_1 | “requestId”: “d2092ece-e906-4351-bdcc-28688ba92990”,
squidex_1 | “requestPath”: “/identity-server/connect/token”,
squidex_1 | “requestMethod”: “POST”
squidex_1 | },
squidex_1 | “timestamp”: “2018-11-18T11:49:18.1513713Z”
squidex_1 | }
squidex_1 |