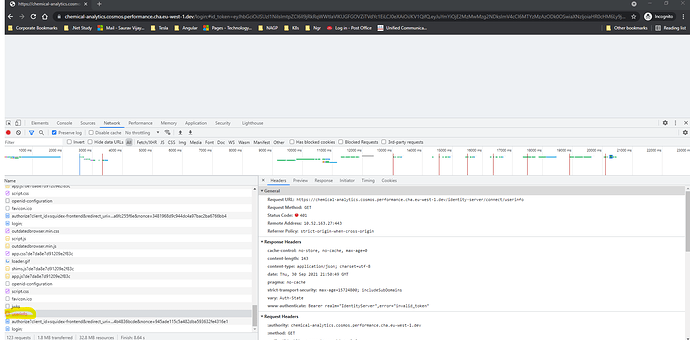
I have two warnings:
Hosting environment: Production
Content root path: /app
Now listening on: http://[::]:80
Application started. Press Ctrl+C to shut down.
{
"logLevel": "Warning",
"message": "Remote socket closed while receiving connection preamble data from endpoint 10.244.0.220:33677.",
"eventId": {
"id": 101307
},
"app": {
"name": "Squidex",
"version": "1.0.0.0",
"sessionId": "a7392fd3-43f1-4e85-ac73-be316c4cd895"
},
"timestamp": "2018-12-06T14:50:46.8567273Z",
"category": "Orleans.Runtime.Messaging.IncomingMessageAcceptor"
}
{
"logLevel": "Warning",
"message": "Exception getting a sending socket to endpoint S10.244.0.220:11111:281803837",
"eventId": {
"id": 101021
},
"exception": {
"type": "System.TimeoutException",
"message": "Connection to 10.244.0.220:11111 could not be established in 00:00:05",
"stackTrace": " at Orleans.Runtime.SocketManager.Connect(Socket s, IPEndPoint endPoint, TimeSpan connectionTimeout)\n at Orleans.Runtime.SocketManager.SendingSocketCreator(IPEndPoint target)\n at Orleans.Runtime.LRU`2.Get(TKey key)\n at Orleans.Runtime.Messaging.SiloMessageSender.GetSendingSocket(Message msg, Socket& socket, SiloAddress& targetSilo, String& error)"
},
"app": {
"name": "Squidex",
"version": "1.0.0.0",
"sessionId": "a7392fd3-43f1-4e85-ac73-be316c4cd895"
},
"timestamp": "2018-12-06T14:50:53.6180040Z",
"category": "Runtime.Messaging.SiloMessageSender/PingSender"
}
0 errors.
And the rest are "logLevel": "Information". Here are the authentication part:
"logLevel": "Information",
"elapsedRequestMs": 388,
"app": {
"name": "Squidex",
"version": "1.0.0.0",
"sessionId": "b1bb4b50-6df4-4f11-9582-7a507896d9eb"
},
"web": {
"requestId": "1449b7f2-4be0-4b49-a52c-f0ac1aa09033",
"requestPath": "/identity-server/connect/authorize",
"requestMethod": "GET"
},
"timestamp": "2018-12-06T14:51:08.0062848Z"
}
{
"logLevel": "Information",
"message": "Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryEndpoint for /.well-known/openid-configuration",
"endpointType": "IdentityServer4.Endpoints.DiscoveryEndpoint",
"url": "/.well-known/openid-configuration",
"app": {
"name": "Squidex",
"version": "1.0.0.0",
"sessionId": "b1bb4b50-6df4-4f11-9582-7a507896d9eb"
},
"web": {
"requestId": "b55b109b-ad14-471b-b3ab-e2759ddec954",
"requestPath": "/.well-known/openid-configuration",
"requestMethod": "GET"
},
"timestamp": "2018-12-06T14:58:19.1093140Z",
"category": "IdentityServer4.Hosting.IdentityServerMiddleware"
}
{
"logLevel": "Information",
"elapsedRequestMs": 1,
"app": {
"name": "Squidex",
"version": "1.0.0.0",
"sessionId": "b1bb4b50-6df4-4f11-9582-7a507896d9eb"
},
"web": {
"requestId": "b55b109b-ad14-471b-b3ab-e2759ddec954",
"requestPath": "/identity-server/.well-known/openid-configuration",
"requestMethod": "GET"
},
"timestamp": "2018-12-06T14:58:19.1096497Z"
}
{
"logLevel": "Information",
"message": "Invoking IdentityServer endpoint: IdentityServer4.Endpoints.AuthorizeEndpoint for /connect/authorize",
"endpointType": "IdentityServer4.Endpoints.AuthorizeEndpoint",
"url": "/connect/authorize",
"app": {
"name": "Squidex",
"version": "1.0.0.0",
"sessionId": "b1bb4b50-6df4-4f11-9582-7a507896d9eb"
},
"web": {
"requestId": "ff785c2a-9053-4124-aec1-d40899e882f0",
"requestPath": "/connect/authorize",
"requestMethod": "GET"
},
"timestamp": "2018-12-06T15:00:45.5149595Z",
"category": "IdentityServer4.Hosting.IdentityServerMiddleware"
}
{
"logLevel": "Information",
"message": "ValidatedAuthorizeRequest\n{\n \"ClientId\": \"squidex-frontend\",\n \"ClientName\": \"squidex-frontend\",\n \"RedirectUri\": \"https://squidex.mydomain.com/client-callback-popup\",\n \"AllowedRedirectUris\": [\n \"https://squidex.mydomain.com/login;\",\n \"https://squidex.mydomain.com/client-callback-silent\",\n \"https://squidex.mydomain.com/client-callback-popup\"\n ],\n \"SubjectId\": \"5bacce9c5935680001f6cba6\",\n \"ResponseType\": \"id_token token\",\n \"ResponseMode\": \"fragment\",\n \"GrantType\": \"implicit\",\n \"RequestedScopes\": \"squidex-api openid profile email squidex-profile role permissions\",\n \"State\": \"1da10ecc55054fb08e9d9386748155f7\",\n \"Nonce\": \"a8a0b32ca75d4f9e8350f4a14709d655\",\n \"DisplayMode\": \"popup\",\n \"SessionId\": \"cc102dadccf5a05a1020158768b4d7f0\",\n \"Raw\": {\n \"client_id\": \"squidex-frontend\",\n \"redirect_uri\": \"https://squidex.mydomain.com/client-callback-popup\",\n \"response_type\": \"id_token token\",\n \"scope\": \"squidex-api openid profile email squidex-profile role permissions\",\n \"state\": \"1da10ecc55054fb08e9d9386748155f7\",\n \"nonce\": \"a8a0b32ca75d4f9e8350f4a14709d655\",\n \"display\": \"popup\"\n }\n}",
"validationDetails": "{\n \"ClientId\": \"squidex-frontend\",\n \"ClientName\": \"squidex-frontend\",\n \"RedirectUri\": \"https://squidex.mydomain.com/client-callback-popup\",\n \"AllowedRedirectUris\": [\n \"https://squidex.mydomain.com/login;\",\n \"https://squidex.mydomain.com/client-callback-silent\",\n \"https://squidex.mydomain.com/client-callback-popup\"\n ],\n \"SubjectId\": \"5bacce9c5935680001f6cba6\",\n \"ResponseType\": \"id_token token\",\n \"ResponseMode\": \"fragment\",\n \"GrantType\": \"implicit\",\n \"RequestedScopes\": \"squidex-api openid profile email squidex-profile role permissions\",\n \"State\": \"1da10ecc55054fb08e9d9386748155f7\",\n \"Nonce\": \"a8a0b32ca75d4f9e8350f4a14709d655\",\n \"DisplayMode\": \"popup\",\n \"SessionId\": \"cc102dadccf5a05a1020158768b4d7f0\",\n \"Raw\": {\n \"client_id\": \"squidex-frontend\",\n \"redirect_uri\": \"https://squidex.mydomain.com/client-callback-popup\",\n \"response_type\": \"id_token token\",\n \"scope\": \"squidex-api openid profile email squidex-profile role permissions\",\n \"state\": \"1da10ecc55054fb08e9d9386748155f7\",\n \"nonce\": \"a8a0b32ca75d4f9e8350f4a14709d655\",\n \"display\": \"popup\"\n }\n}",
"app": {
"name": "Squidex",
"version": "1.0.0.0",
"sessionId": "b1bb4b50-6df4-4f11-9582-7a507896d9eb"
},
"web": {
"requestId": "ff785c2a-9053-4124-aec1-d40899e882f0",
"requestPath": "/connect/authorize",
"requestMethod": "GET"
},
"timestamp": "2018-12-06T15:00:45.5163785Z",
"category": "IdentityServer4.Endpoints.AuthorizeEndpoint"
}
{
"logLevel": "Information",
"message": "Authorize endpoint response\n{\n \"SubjectId\": \"5bacce9c5935680001f6cba6\",\n \"ClientId\": \"squidex-frontend\",\n \"RedirectUri\": \"https://squidex.mydomain.com/client-callback-popup\",\n \"State\": \"1da10ecc55054fb08e9d9386748155f7\",\n \"Scope\": \"openid profile email squidex-profile role permissions squidex-api\"\n}",
"response": "{\n \"SubjectId\": \"5bacce9c5935680001f6cba6\",\n \"ClientId\": \"squidex-frontend\",\n \"RedirectUri\": \"https://squidex.mydomain.com/client-callback-popup\",\n \"State\": \"1da10ecc55054fb08e9d9386748155f7\",\n \"Scope\": \"openid profile email squidex-profile role permissions squidex-api\"\n}",
"app": {
"name": "Squidex",
"version": "1.0.0.0",
"sessionId": "b1bb4b50-6df4-4f11-9582-7a507896d9eb"
},
"web": {
"requestId": "ff785c2a-9053-4124-aec1-d40899e882f0",
"requestPath": "/connect/authorize",
"requestMethod": "GET"
},
"timestamp": "2018-12-06T15:00:45.5222509Z",
"category": "IdentityServer4.Endpoints.AuthorizeEndpoint"
}