I have…
- Read the following guideline: Troubleshooting and Support | Squidex. I understand that my support request might get deleted if I do not follow the guideline.
- Used code blocks with ``` to format my code examples like JSON or logs properly.
I’m submitting a…
- Regression (a behavior that stopped working in a new release)
- Bug report
- Performance issue
- Documentation issue or request
Current behavior
Hello.
I’m currently making changes to a website that uses Squidex as its backend. During a recent security analysis conducted by an external security team, a concern was raised regarding the GraphQL endpoint and its introspection capabilities.
They mentioned the following:
GraphQL exposed with active introspection, allowing access to the web application schema;
Public queries available, allowing the recovery of all assets through the GraphQL endpoint;
There are potentially intrusive mutations, but they have not been tested due to lack of authorization.
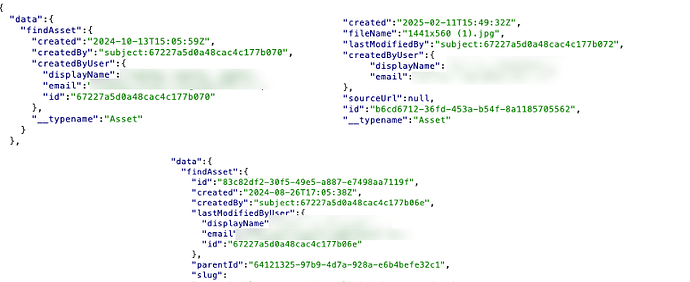
Here is an example of personal information that was exposed:
Is there a way to restrict or disable introspection in Squidex? What would be the recommended best practices to address this kind of exposure?
Thanks
Expected behavior
Minimal reproduction of the problem
Environment
App Name:
- Self hosted with docker
- Self hosted with IIS
- Self hosted with other version
- Cloud version
Version: [VERSION]
Browser:
- Chrome (desktop)
- Chrome (Android)
- Chrome (iOS)
- Firefox
- Safari (desktop)
- Safari (iOS)
- IE
- Edge
Others: