Hi Sebastian,
Squidex is running on https://localhost:8443/. Based on this, what is the correct Redirect URI to use on the application registration on Azure?
Sorry for the simple question but after a few attempts and seemingly not a word about this in the docs I quickly grew tired of guessing.
I think it should be /identity-server/signin-oidc
Are you sure about this? Because:
There are several methods to configure oidc for Azure AD. If you use the microsoft integration, then it is signin-microsoft
I see. I simply created an app reg in Azure and filled in the SQUIDEX_MICROSOFTCLIENT and SQUIDEX_MICROSOFTSECRET values in the .env file. This works with /identity-server/signin-microsoft. Which other methods are there to integrate with Azure AD with Squidex?
All providers (Google, Microsoft, Github) are just OIDC providers and the integration uses a general code base for OIDC and sets some defaults.
But you can also go the rocky way and set it up manually: https://github.com/Squidex/squidex/blob/master/backend/src/Squidex/appsettings.json#L507
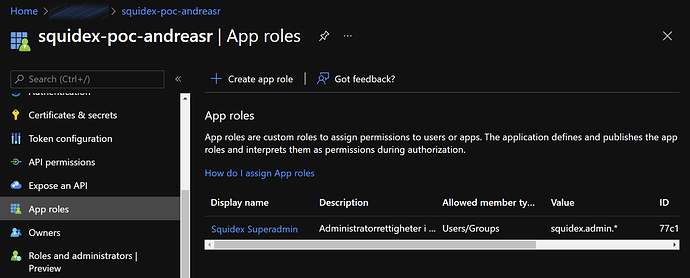
I understand. Do you know if it is possible to configure app roles in Azure in a manner that will help Squidex understand the credentials of the person logging in?
I tried creating an app role like this:
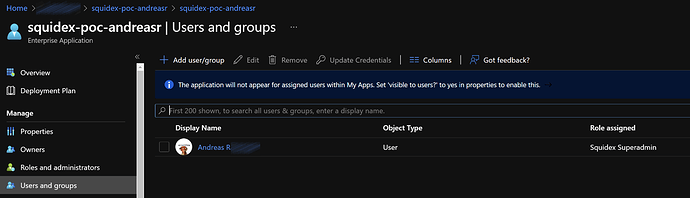
And then assigning my user to this role for the app through “Enterprise Apps”:
But when I log in to Squidex it is obvious that this is not enough to make Squidex recognize the admin claim for my user. Do you know which other steps I need to make to have this work as intended?
Squidex uses this claims: https://github.com/Squidex/squidex/blob/master/backend/src/Squidex.Shared/Identity/SquidexClaimTypes.cs#L28
I think you can assign them and Squidex should copy them over, but only during the first login.
Otherwise it would be necessary to call the Azure AD service for each request.
Hm, I see. It’s not clear to me where to specify this claim type in Azure. Do you know how to do this?
No, sorry. I am Google Cloud user