I have…
- [ x ] Checked the logs and found some error logs below:
CleanupDefunctSiloEntries operation is not supported by the current implementation of IMembershipTable. Disabling the timer now.
Showing error: prompt=none was requested but user is not authenticated
JWT token validation error: IDX10501: Signature validation failed. Unable to match key: \nkid: \u0027[PII is hidden.
Error validating JWT\n{\n \u0022ClientId\u0022: \u0022squidex-frontend\u0022,\n \u0022ClientName\u0022: \u0022squidex-frontend\u0022,\n \u0022ValidateLifetime\u0022: false\n}","@logMessage":"{\n \u0022ClientId\u0022: \u0022squidex-frontend\u0022,\n \u0022ClientName\u0022: \u0022squidex-frontend\u0022,\n \u0022ValidateLifetime\u0022: false
End session request validation failure: Error validating id token hint\n{\n \u0022SubjectId\u0022: \u0022unknown\u0022,\n \u0022Raw\u0022: {\n \u0022id_token_hint\u0022: \u0022***REDACTED***\u0022,\n \u0022post_logout_redirect_uri\u0022
Error processing end session request Invalid request",“error”:“Invalid request”,“app”:{“name”:“Squidex”,“version”:“4.2.0.0”,“sessionId”:“e632846c-5d00-42d4-9f49-fc1b04d9a0d8”},“web”:{“requestId”:"|8a69e932-4cfbf5ee0ee59176.",“requestPath”:"/connect/endsession",“requestMethod”:“GET”},“timestamp”:“2020-04-23T01:51:37Z”,“category”:“IdentityServer4.Endpoints.EndSessionEndpoint”}
I’m submitting a…
- [ x ] Regression (a behavior that stopped working in a new release)
- [ x ] Bug report
- [ ] Performance issue
- [ x ] Documentation issue or request
Current behavior
Below issues are tested and found on version 4.0.3 and 4.2.
Permission label undefine issue is only on v4.2 custom roles. Default systems roles’ permission labels display fine in v4.2.
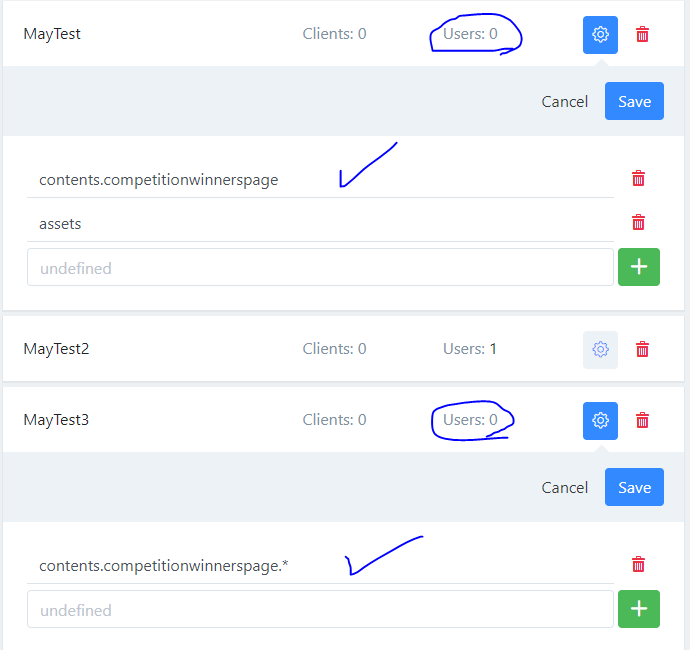
- v4.2 specific Custom role permission labels are not displaying when a user is assigned to the role. See attached images:
Permission labels without assign users:
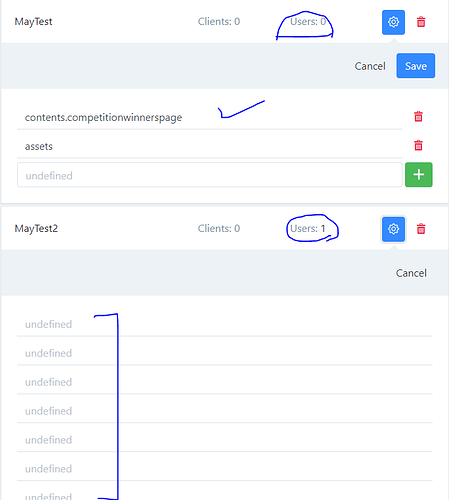
Permission labels with assigned users
- Custom roles with permission * wildcard on sections no longer work
- User cannot perform allowed action(s) (read/create/update) if assigned with custom roles
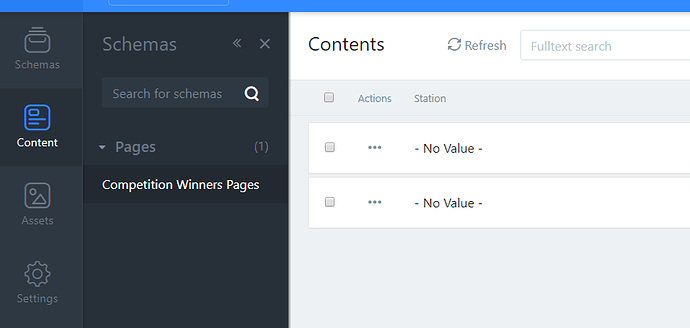
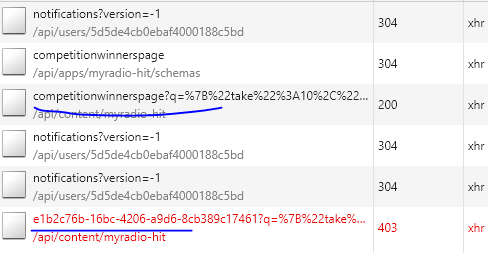
Content list(if available) is displaying as ‘- No Value -’. Redirect to forbidden page when create/read the content. See attached image. - Custom roles permissions cannot be updated
Expected behavior
- Custom roles which has assigned users should display permissions labels instead of undefine in v4.2
- Wildcard on sections should work as per documentation https://docs.squidex.io/02-documentation/concepts/permissions#defining-permissions.
eg: contents.xxx.* , contents.pages|posts|articles.* - When a user is assigned with a custom role to restrict access for specific content schema management, the user should be able to access allowed content section and should be able to perform allowed action(s)
- Should be able to update custom roles with/without users permissions, not just delete them while it has no users assigned
Minimal reproduction of the problem
Provided there are multiple content schemas available, create a new custom role to only allow one schema management. eg. page content.
Role test 1 permissions:
- contents.page
- assets
Role test 2 permissions:
- contents.page.*
Role test 3 permissions:
- contents.page.read
- contents.page.create
- contents.page.update
- contents.page.delete
- contents.page.update.partial
- contents.page.version.create
- contents.page.version.delete
Role test 4 permissions:
- contents.page
- all of the permissions above from test 3
Environment
- [ x ] Self hosted with docker
- [ ] Self hosted with IIS
- [ ] Self hosted with other version
- [ ] Cloud version
Version:
- 4.0.3.0
- 4.2
Browser:
- [ x ] Chrome (desktop)
- [ ] Chrome (Android)
- [ ] Chrome (iOS)
- [ ] Firefox
- [ ] Safari (desktop)
- [ ] Safari (iOS)
- [ ] IE
- [ ] Edge
Others:
Similar issues reported on: [SOLVED] Custom roles issue
Also it’ll be really great if there’s permission to NOT allow using ^ as mentioned in the documentation or able to hide schema or settings sections as it’s really not right to let user who should only see one content schema section able to view the whole site schemas in the schema section including json, settings tabs.